In this document, we will cover some basic information about security and best practices that you can implement to reduce your risk of identity theft or loss of control over your system.
Logging onto systems
One of the most common mistakes people make is signing into the wrong website, the scenario is simple you get an email it says something to make you log into some service and the page looks like the one you expect so you pop in your email address and password and wham it all goes pear shaped. A list of common attacks and the correct method of dealing with them follows:
| Software Updates | These never need to come via email, if a vendor has a software update you can always go to their site and get the download, no need to click any link in an email and normally no need to log in anywhere. The best example of this is adobe acrobat reader this is free software and it updates itself all you need do is open the app from your computer (normally sitting on your desktop) and if it needs to update itself it will tell you. |
| Email Attachments | If you get an unsolicited email with an attachment just delete it if it's really important the person will call or contact you to let you know something is heading your way |
| Flash drives | If you have used a flash drive in someone else's computer watch out, and doubly watch out if you have been overseas and plugged in somewhere these devices are not secured |
| Wi-Fi | IS NOT SECURE never has been never will be. NO the password does NOT make it secure they might as well all be set to password as any user can download a tool to decrypt the Wi-Fi key and then they know the password for the Wi-Fi |
| Any person can masquerade as anyone they like on email and only a skilled tech can tell the difference | |
| Web Browsing | 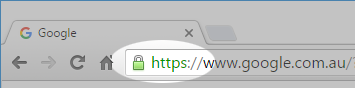 Is only secure if you can see the padlock in the address bar make yourself familiar with this feature it actually means something quite important. Is only secure if you can see the padlock in the address bar make yourself familiar with this feature it actually means something quite important. |
Correct login method for a "login with" option is as follows:
- If you go to a site and it offers "login via Facebook" functionality, firstly open a new window and navigate to Facebook.com login as normal and leave the window open, now go back to your chosen site and click the Login via Facebook option you should not be prompted to put in your email address or password just a prompt for the "can we invade your privacy by capturing your email etc. message" if you are prompted for email and password then be careful ... because that's not how it's supposed to work.
- Log in with Google; these days everyone has a Google account and this is a simple and secure method of navigating in and out of services as you can go to Google.com log in and work all day without re-entering your logon credentials (unless you close out of your internet session of course). But again you need to be sure you are not plugging in your details on the wrong site, a good example of how this should work is our site, we use login with Google and this saves the hassle of you setting up an account with us as we grab your email address and name from google and you never need to use a password as we have a trust relationship with Google. How is this good for you well you don't need you to provide a password to access data on this website in addition, we don't need to store or reset passwords as Google manage this for you. Basically, you don't have an account with us you have one with google at our end it's just a login.
- Login with Live; well you get the idea by now so login to live.com first then back to the page you started with.
Passwords
This is the number one issue for most users, they basically have too many passwords and in an effort to keep things secure resort to using password managers or storing the passwords in an electronic format a hackers dream.
Here is a guide on how to create a good set of passwords that can be used in all areas of your life online and if followed should reduce the need to weaken security by writing passwords down.
Firstly you need 4 passwords, no more no less.
Start by picking a word you won't forget:
- Any word you like but must not be your name or any part of it
- Must be between 8 and 10 characters long
Now we need to modify the word meet system password policies for example:
| Word: | technology | Pick something easy to remember |
| Add a capital | TechNology | Capitalise it doesn't need to be the first capitalise on a syllable if you like |
| Add a number | TechN0l0gy | Common number changeouts vowels A=4 E=3 I=1 O=0 |
| Add a special character | TechN0l0gy! | End result |
Now we have our obfuscation method it's time to create 4 unique passwords and we need to categorise the usage so we are sure we know which to use when. The two most critical areas are banking and email and these two passwords must never be the same and never written down so from most secure to least secure and note the banking password is not one of these. For banking, you know the method pick something obscure memorise it and only use it with a bank and never anywhere else.
| First: Very Secret | Tech-N0l0gy! | Use for email or any system that manages your identity, remember most systems send password resets to your primary email address so an attacker is targeting this account. Once someone has control of your email they can slowly take over everything. |
| Second: Wouldn't want anyone to guess this one | #1TechNology | Use this for everything that you make payments online with e.g. mobile phone service provider, shopping sites or subscriptions to services,basically anywhere money could change hands or where enough info is stored to represents a risk to you of identity theft. The key things someone needs to know about you are full legal name, date of birth, home address |
| Third: no big deal if someone found out | TechR0cks$ | The main password for daily use, easy to remember and used everywhere you plan to go back to, but not anywhere you have any financial involvement with e.g. use it for Facebook, Skype, LinkedIn all the social stuff |
| Fourth: might have to disclose to a third party or share it | ILoveTech123 | A throwaway password, it can be emailed or disclosed if required don't use it anywhere important e.g. use it when registering online for free stuff or where a password is required but you don't really expect to go to the site that often and where security is not an issue. |
Notes:
- Bank security is the highest there is so it's reasonably safe to use the same password for more than one account if you are careful how you use it and keep a list of the banking hotline numbers so you can quickly contact all banks in the event of a fraud attack to get your account password reset.
- Some systems require a password change on a regular basis so just increment a number on the end e.g. Techn0l0gy1! / Techn0l0gy2! / Techn0l0gy3!
- Some systems don't allow special characters e.g. Techn0l0gy
Common sense is the key to safety online if it feels wrong just don't do it, trust your instincts and if in doubt close the window or log out of the site but to be clear:
- Never click the link.
- Don't open the attachment.
- Don't go to the website and login
- There is no such thing as free "anything"
- You have not been selected to win anything "ever"
- Nobody needs your help "online"
- There is no such thing as a quick $$$
- The email from Microsoft, Australia Post, The Government, The ATO is a fake
- There is no new virus that people don't already know about
- The popup window that came up saying you have a problem with your PC is lying to you and clicking it will give you a problem
I don't know how many times I have fixed PC's for the above issues but it numbers in the thousands so after 20+ years in IT all I can say is a 2-minute call to the helpdesk will head off days of heartache and loss of personal data, I can guarantee you that clicking a link in an email can completely destroy all your data including your backups, and yes I have seen it happen. The user had left the backup drive connected to the computer as the malware hit the first thing it did was encrypted the ".bkf" file it was actively looking for backups as its first order of business. And "NO" I do not know why these people write this malicious software but if I could get my hands on them I would probably end up in prison for GBH or worse.